iOS Clipboard Privacy Concerns|Balancing Security and Convenience
Discover why numerous iOS apps access your clipboard, exposing privacy risks. Learn actionable insights to protect your data while maintaining app functionality and convenience.
This post was translated with AI assistance — let me know if anything sounds off!
Table of Contents
iOS 14 Clipboard Data Theft Panic: The Privacy vs. Convenience Dilemma
Why Do So Many iOS Apps Read Your Clipboard?
Photo by Clint Patterson
⚠️ 2022/07/22 Update: iOS 16 Upcoming Changes
Starting from iOS 16, if the paste action is not initiated by the user, the app’s active reading of the clipboard will trigger a prompt. The user must allow it for the app to access the clipboard data.
UIPasteBoard’s privacy change in iOS 16
Issue
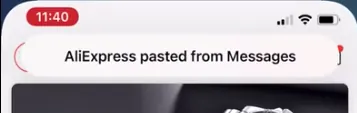
Top notification message when the clipboard is accessed by an app
Starting with iOS 14, users are notified when an app reads their clipboard. Apps from mainland China have a notorious reputation, and media coverage has amplified privacy concerns. However, it’s not just Chinese apps; many apps from the US, Taiwan, Japan, and around the world have been caught. So why do so many apps need to read the clipboard?
Google Search
Security
The clipboard may contain personal privacy information or even passwords, such as when copying passwords from password managers like 1Password or LastPass. If an app can read the clipboard, it can also send that data back to a server. It all depends on the developer’s integrity. To investigate, you can use man-in-the-middle sniffing to monitor whether the app sends clipboard data back to the server.
Background
Clipboard API has been available since iOS 3 in 2009. However, starting from iOS 14, users receive additional prompts notifying them. Over the past decade, malicious apps could have already collected enough data.
Why
Why do so many apps, both domestic and international, read the clipboard when opened?
Here, I need to clarify that the situation I’m referring to is “when the APP is opened,” not reading the clipboard while the APP is in use; reading the clipboard during app use is more related to in-app features, like Google Maps automatically pasting a recently copied address, though some apps might continuously steal clipboard data.
“A kitchen knife can be used to cut vegetables or to kill, depending on how the person uses it.”
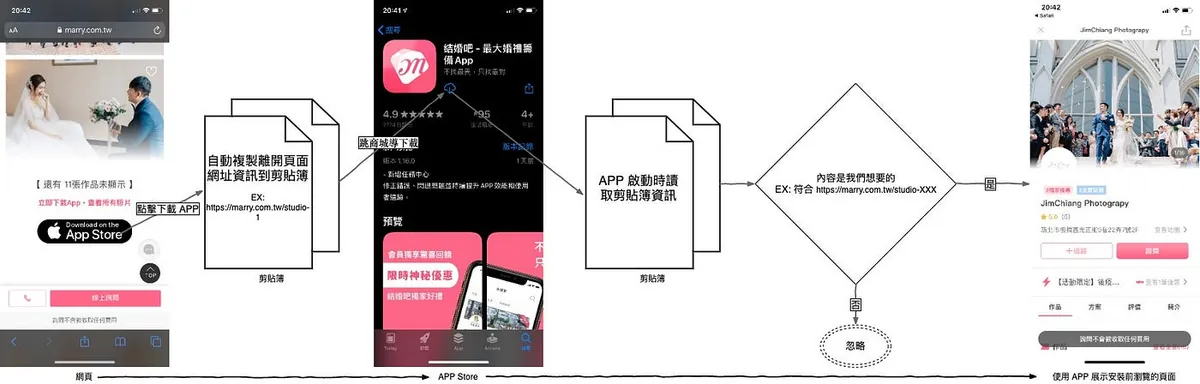
The main reason the app reads the clipboard on launch is to implement iOS Deferred Deep Link to enhance user experience, as shown in the above process. When a product offers both a website and an app, we prefer users to install the app (due to higher engagement). Therefore, when users browse the web version, they are guided to download the app, and we want the app to automatically open the page they left off on when launched after installation.
EX: When I browse the PxHome mobile website on Safari -> see a product I like and want to buy -> PxHome wants to drive traffic to the APP -> download the APP -> open the APP -> display the product I just saw on the website
If this is not done, users can only 1. go back to the webpage and click again, or 2. search for the product again within the app; both options increase the difficulty and hesitation time for users to make a purchase, which may lead to them not buying at all!
On the other hand, from an operational perspective, knowing the statistics of successful installs by source greatly aids marketing and advertising budget allocation.
Why must we use the clipboard? Are there any alternatives?
This is a cat-and-mouse game because iOS itself does not want developers to reverse-track user sources. Before iOS 9, the method was to store information in web cookies, then read the cookies after the app was installed. After iOS 10, Apple blocked this method. With no other options left, everyone resorted to the final technique — “transmitting information via the clipboard.” iOS 14 introduced a new move again, notifying users and putting developers in an awkward position.
Another approach is to use Branch.io to track user profiles (IP, device information), then merge the data for retrieval. This method is feasible in principle but requires significant manpower (involving backend, database, and app development) for research and implementation, and it may result in misjudgments or collisions.
The Android Google app natively supports this feature, no workaround needed like on iOS.
Affected Apps
Many app developers may not realize they also have clipboard privacy issues because Google’s Firebase Dynamic Links service works on the same principle:
1
2
3
4
5
// This string ensures that only FDL links copied to the clipboard by the AppPreview Page
// JavaScript code are recognized and used in the copy-unique-match process. If the user
// copies the FDL to the clipboard manually, that link must not be used in the copy-unique-match process.
// This constant must be kept in sync with the constant in the server version at
// durabledeeplink/click/ios/click_page.js
So any app using Google Firebase Dynamic Links service may be affected by clipboard privacy issues!
Personal Viewpoint
Security issues do exist, but it comes down to trust—trusting that developers use it for the right purposes. If developers intend to do harm, there are many easier ways to do so, such as stealing credit card information or recording actual passwords, which are far more effective than this.
The purpose of the prompt is to alert users when the clipboard is being accessed; if the timing seems unusual, they should be cautious!
Reader’s Question
Q: Is the statement “TikTok accesses the clipboard to detect spam behavior” accurate?
A: I personally think it’s just an excuse to appease public opinion. Douyin probably means “to prevent users from copying and pasting ads everywhere.” But in reality, blocking or filtering can be done when the message is completed or sent. There’s no need to constantly monitor the user’s clipboard! Should they also control ads or “sensitive” content in the clipboard? I haven’t pasted or posted anything.
What Developers Can Do
If you don’t have a spare device to upgrade to iOS 14 for testing, you can first try using the simulator by downloading XCode 12 from Apple.
Everything is still too new. If you are integrating Firebase, you can first refer to Firebase-iOS-SDK/Issue #5893 and update to the latest SDK.
If you implement DeepLink yourself, you can refer to the Firebase-iOS-SDK #PR 5905 modification:
Swift:
1
2
3
4
5
6
7
if #available(iOS 10.0, *) {
if (UIPasteboard.general.hasURLs) {
//UIPasteboard.general.string
}
} else {
//UIPasteboard.general.string
}
Objective-C:
1
2
3
4
5
6
7
8
9
if (@available(iOS 10.0, *)) {
if ([[UIPasteboard generalPasteboard] hasURLs]) {
//[UIPasteboard generalPasteboard].string;
}
} else {
//[UIPasteboard generalPasteboard].string;
}
return pasteboardContents;
}
First check if the clipboard content is a URL (matching the copied content from the webpage JavaScript which includes URL parameters) before reading it. This prevents the clipboard from being read every time the app is opened.
This is the only way for now. The prompt will still jump, but this just makes it more focused.
Apple has also added a new API: DetectPattern, which helps developers more accurately determine if the clipboard content is what they need before reading it and showing prompts. This makes users feel more secure and allows developers to continue using this feature.
DetectPattern is still in Beta and can only be implemented using Objective-C.
Or…
Switch to Branch.io
Implement the Principle of Branch.io by Yourself
The app first displays a customized alert to inform the user, then reads the clipboard (to reassure the user)
Add new privacy policy terms
iOS 14 Latest App Clips? From Web -> Launch Lightweight App Clips -> In-depth APP Operation
Further Reading
If you have any questions or feedback, feel free to contact me.
This post was originally published on Medium (View original post), and automatically converted and synced by ZMediumToMarkdown.

{:target="_blank"}](/assets/8a04443024e2/0*pOtqMDY0qXhDJXXG.webp)